
A tech expert has broken down 'clues' within a sophisticated phishing email which has been sent to Gmail users from a 'valid, signed email'.
Founder of Ethereum Name Service, Nick Johnson, took to Twitter last month to raise awareness of 'an extremely sophisticated phishing attack' explaining it 'exploits a vulnerability in Google's infrastructure'.
And given cybersecurity company Kaspersky shared an article about it last week, it would seem the attack is ongoing - UNILAD has contacted Google for comment.
Johnson took to Twitter on April 16 to share screenshots of the email he received, analysing the images explaining just how advanced the phishing attack is.
Advert

What does the 'no-reply' phishing email looks like?
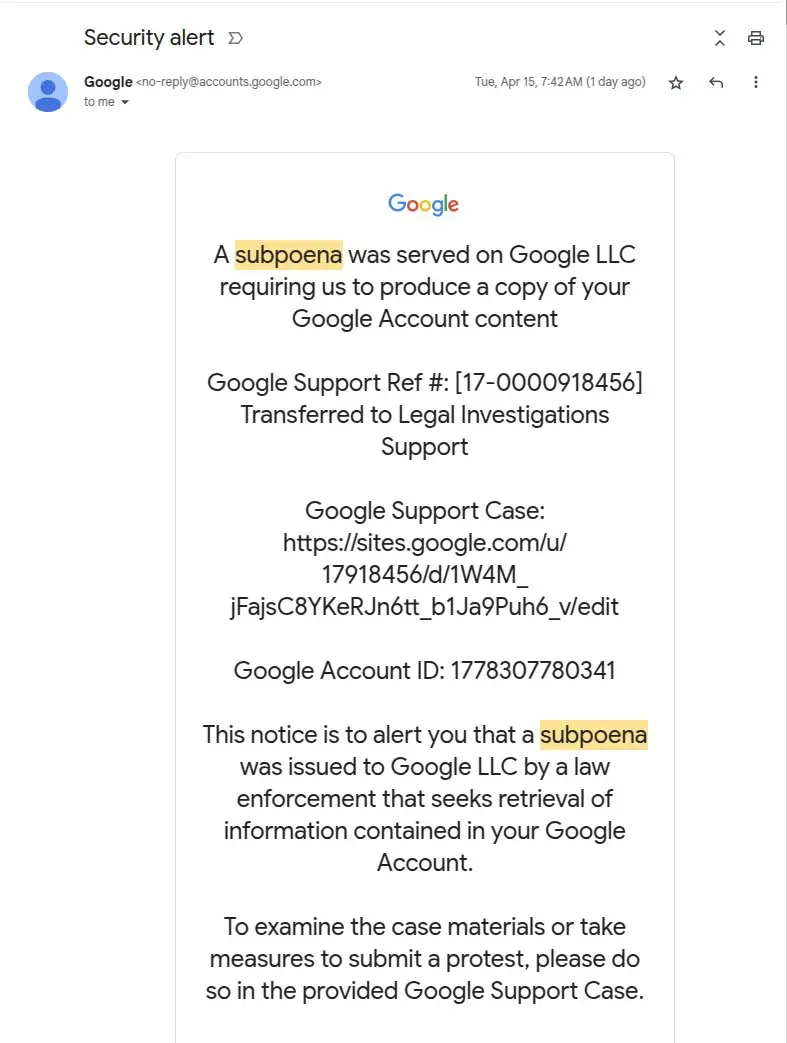
The 'first thing to note'? A 'valid, signed email'.
"It really was sent from [email protected]," he explains. "It passes the DKIM signature check, and GMail displays it without any warnings - it even puts it in the same conversation as other, legitimate security alerts."
Not only this, but the 'Sites link' then takes you to 'a very convincing 'support portal' page', which has a domain which looks 'legit' too.
Should you then click on 'Upload additional documents' or 'View case', you'd also be taken to a 'signin page' which is 'an exact duplicate of the real thing'.
"The only hint it's a phish is that it's hosted on http://sites.google.com instead of http://accounts.google.com," he adds.
Johnson theorized the scam works in 'harvest[ing] your login credentials' should you put them in and then 'use them to compromise your account'.
Unsurprisingly, he didn't go further to check.
But how was the phishing attack able to make itself look so believable?
How does the phishing 'no-reply' email look so 'convincing'?
Essentially, the phishers register a domain, create a Google account for 'me@domain' and then create a Google OAuth application where they enter the Phishing message alongside some whitespace and 'Google Legal Support'.
"Now they grant their OAuth app access to their 'me@...' Google account. This generates a 'Security Alert' message from Google, sent to their 'me@...' email address. Since Google generated the email, it's signed with a valid DKIM key and passes all the checks," Johnson explains.
The scammers then 'forward the message to their victims' and 'because DKIM only verifies the message and its headers and not the envelope, the message passes signature validation and shows up as a legitimate message in the user's inbox - even in the same thread as legit security alerts'.
"Because they named their Google account 'me@', GMail shows the message was sent to 'me' at the top, which is the shorthand it uses when a message is addressed to your email address - avoiding another indication that might send up red flags," he resolves.
And how this is possible? Well, Johnson argues it's down to 'two vulnerabilities in Google's infra[structure]'.
The 'two vulnerabilities in Google infrastructure'
Johnson explains the 'fake portal is fairly straightforward' as users can 'host content on a http://google.com subdomain'.
Johnson says there's 'no way to report abuse from the Sites interface too', meaning it's easier for the phishers to simply upload new versions of 'arbitrary scrips and embeds'.
Johnson recommends Google 'disable scrips and arbitary embeds in Sites' as they're 'too powerful a phishing vector'.
However, he notes the email is 'much more sophisticated'.
So, how did Johnson spot it was dodgy?
How to spot a phishing email
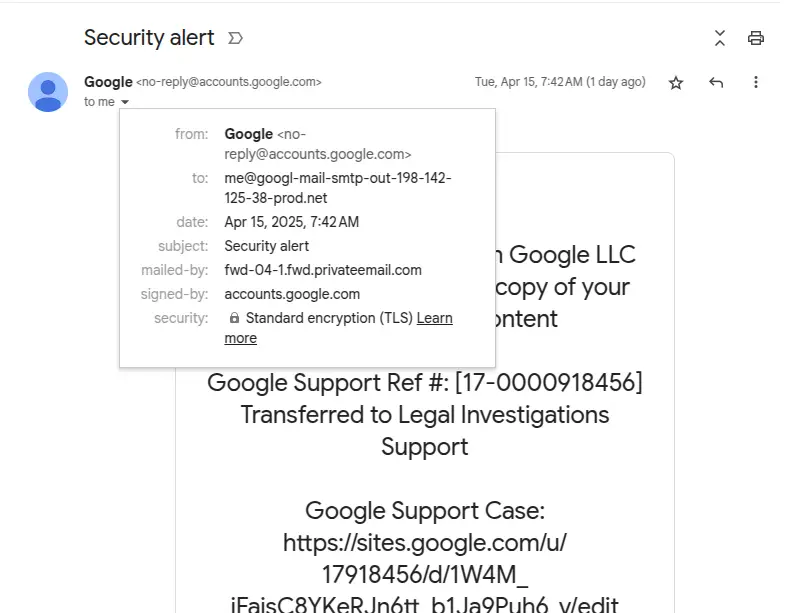
Johnson points out the 'first clues' come with the header of the email.
"Although it was signed by http://accounts.google.com, it was emailed by http://privateemail.com, and sent to 'me@blah,'" he states.
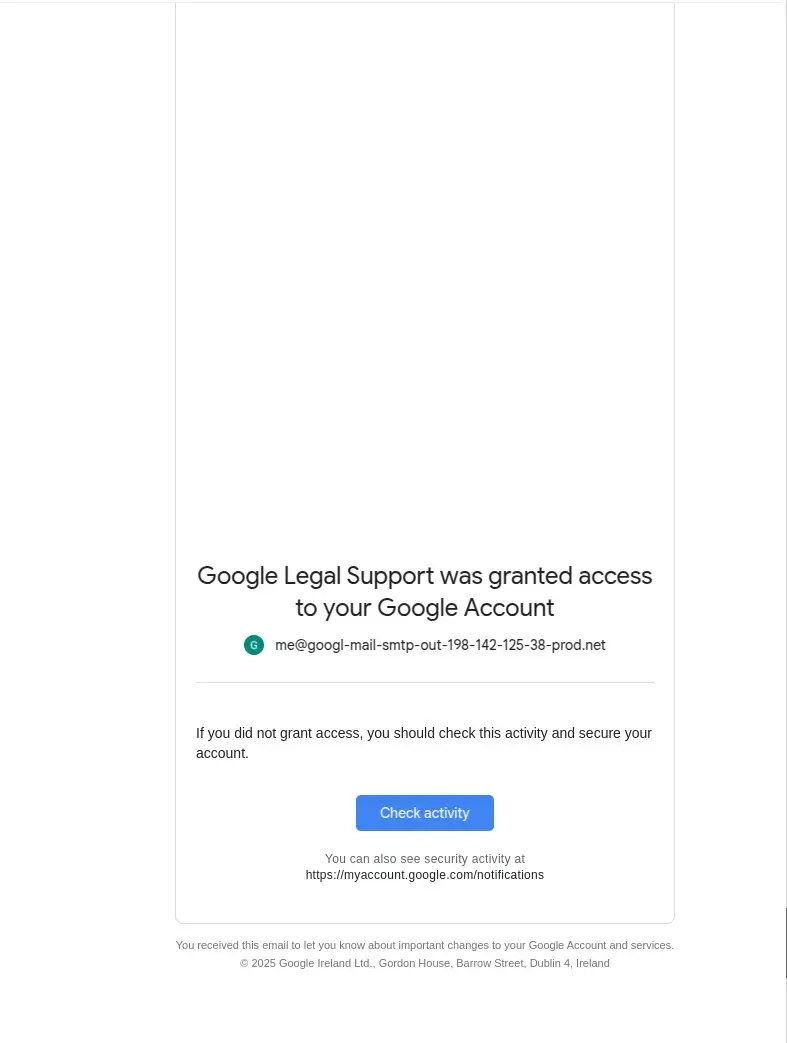
And the 'second clue'? "Below the phishing message is a lot of whitespace (mostly not shown) followed by 'Google Legal Support was granted access to your Google Account' and the odd me@... email address again," Johnson flags.
Johnson notes he's submitted a bug report to Google, later updating Google responded saying it 'will be fixing the oauth bug'.
What Google has said about the 'no-reply' email
A spokesperson from Google told UNILAD: "We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse. In the meantime, we encourage users to adopt two-factor authentication and passkeys, which provide strong protection against these kinds of phishing campaigns."
Topics: Google, Technology, Twitter